
Integrating with AWS
The Satori platform supports integration with various AWS services for example, data asset discovery, authorization analysis and audit log ingestion. The following section descibes how to integrate Satori with various AWS services.
Integrating your AWS account with Satori
The DAC workloads are configured to assume a IAM role, we will refer to this role as the DAC Role principal, formatted as <cluster_name>-role, for example prod-aws-us-east-1-acme-role.
A second role must be configured on the target account, we will refer to this role as the Service Role principal, formatted as
<cluster_name>-service-role, for example prod-aws-us-east-1-acme-service-role.
The integration is based on the DAC Role being able to assume a Service Role which has the required permissions for the selected AWS services.
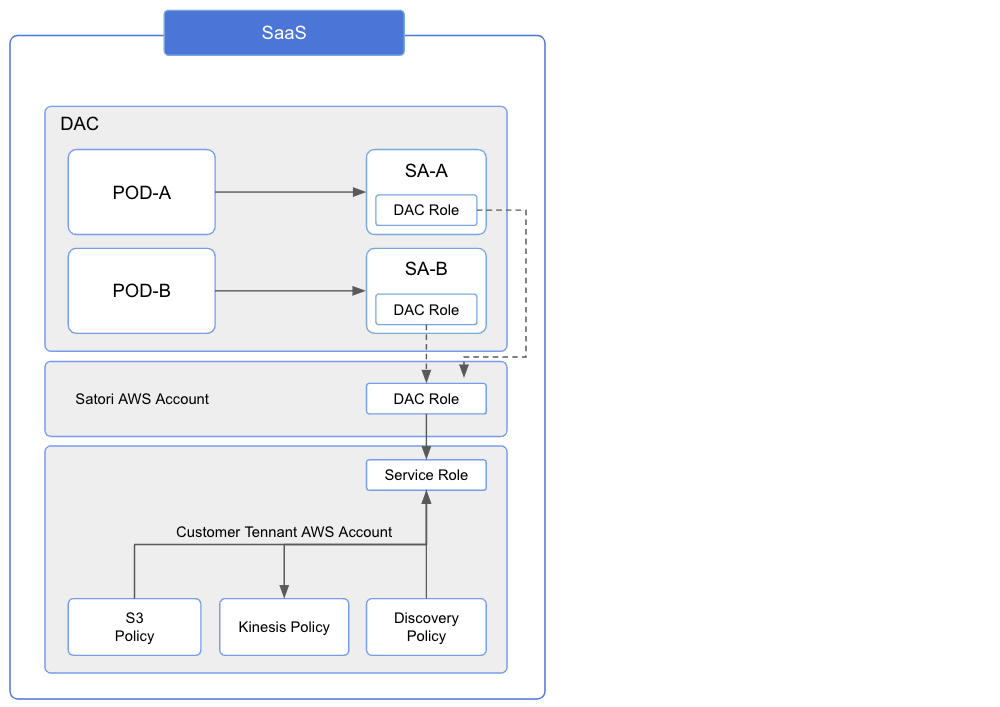
SaaS Deployment
For SaaS based deployment, a DAC Role is pre-provisioned on Satori's AWS account, only the Service Role needs to be set up on the AWS account.
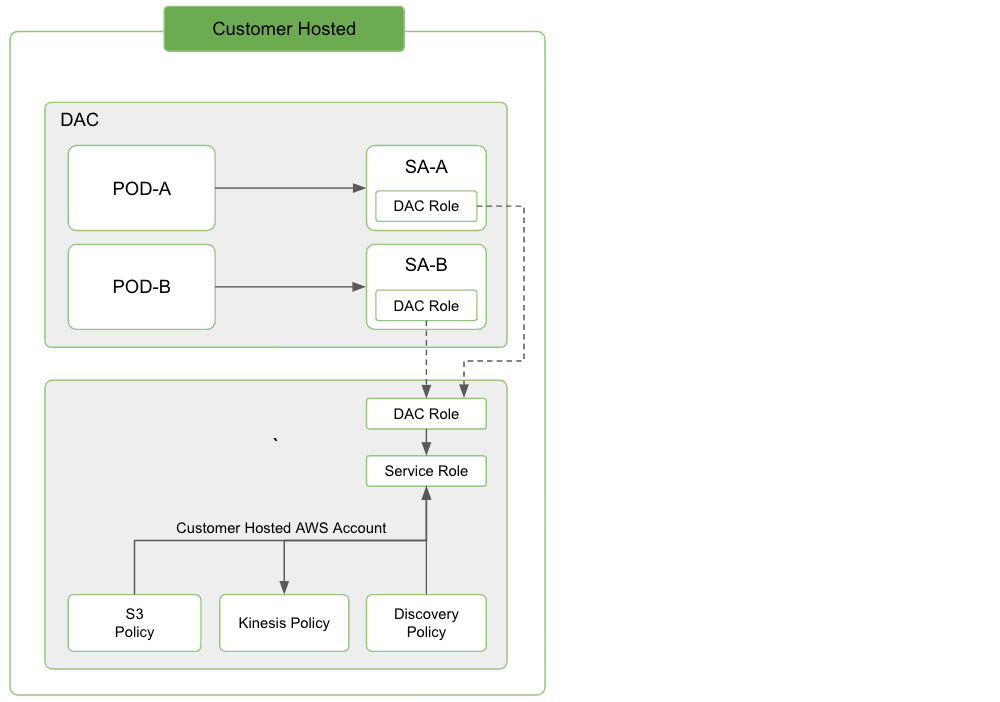
Customer Hosted Deployment
For Customer hosted deployments, both DAC Role and Service Role need to be set up on the AWS account.
Setting up the DAC role (Customer Hosted Deployment only)
For a customer hosted deployment the DAC Role must be configured and attached to the EKS cluster, perform the following steps to create a DAC Role.
When integrating with SaaS DACs, these below steps should be skipped, please continue to the Setting up the Service Role section.
-
Create a DAC Role principal in the format of
<cluster_name>-role, for exampleprod-aws-us-east-1-acme-role. The cluster name is available in the management console under DAC settings. -
Create and Attach a Trust Relationship Policy, The trust relationship policy enables the DAC workloads to assume the DAC Role. The OpenID Connect provider URL address can retrieved from the EKS settings.
Note: OPENID_CONNECT_URL is the EKS cluster's OpenID Connect provider URL without the https prefix.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "SatoriDacRoleTrustPolicy",
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::<DAC_AWS_ACCOUNT_ID>:oidc-provider/<OPENID_CONNECT_URL>"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringLike": {
"<OPENID_CONNECT_URL>:sub": "system:serviceaccount:satori-runtime:*"
}
}
}
]
}
- Create and Attach a Permission Policy, the permission policy is required for the DAC Role to be able to assume the Service Role
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "SatoriDacRolePermissionPolicy",
"Action": [
"sts:AssumeRole"
],
"Effect": "Allow",
"Resource": [
"arn:aws:iam::*:role/<SERVICE_ROLE_NAME>"
]
}
]
}
Setting up the Service Role
- Create a Service Role principal in the format of
<cluster_name>-service-role, for exampleprod-aws-us-east-1-acme-service-role. The cluster name is available in the management console under under DAC settings.
Note: Multiple service roles are required for integrating with multiple accounts.
- Create and Attach a Trust Relationship Policy. To allow the DAC Role to assume the Service Role a trust relationship must be created and attached to the Service Role. The policy must include the externalID condition to provide security against the confused deputy problem, the external ID parameter is located in the account settings.
Note: For On-prem dacs DAC_AWS_ACCOUNT_ID is identical to CUSTOMER_AWS_ACCOUNT_ID
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "SatoriServiceRoleTrustPolicy",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<CUSTOMER_AWS_ACCOUNT_ID>:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "<EXTERNAL_ID>",
"aws:PrincipalArn": [
"arn:aws:iam::<DAC_AWS_ACCOUNT_ID>:role/<DAC_ROLE_NAME>"
]
}
}
}
]
}
- Create and Attach a Permission Policy, To allow the service role access to the relevant AWS services a permission policy must be attached to the Service Role, permission policies are feature specific. The policy details are located in the management console, as part of the feature configuration process. Below is an example for an S3 posture management policy:
{
"Version": "2012-10-17"
"Statement": [
{
"Sid": "SatoriScanning"
"Action": [
"iam:List*",
"iam:Get*",
"s3:List*",
"s3:Get*",
"s3:Describe*",
],
"Effect": "Allow",
"Resource": "*",
}
],
}