Business Intelligence Software
Satori integrates with BI software to monitor and enforce security and privacy policies for data consumers who use BI tools to access data.
To bind the BI tools to Satori they must be connected to the data store via the Satori hostname address.
Learn more about the Satori Data Platform and Schedule a demo meeting
BI Tool - User Data Access
Users utilize BI tools to access data using a single, shared user identity connected to the data store. When the user connects to a data store with a BI tool via Satori, Satori is only aware of a single user entity and is not exposed to the full context of the real end user data access.
The following diagram illustrates how Satori cannot determine that the end user Alice is accessing data via the BI tool, and Satori only sees the shared BI_USER username.
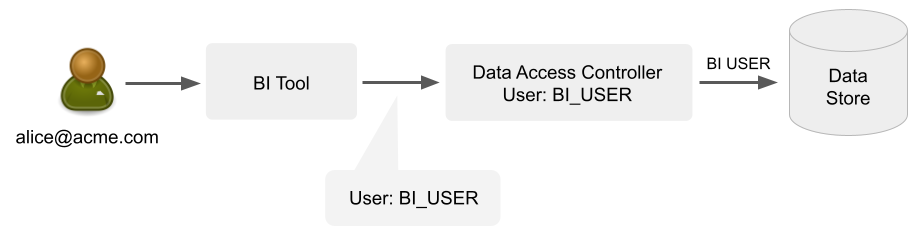
Making Satori Aware of Individual End Users
To enable Satori to be aware of the individual end users accessing data, Satori leverages the existing capabilities of the BI tools. Satori collects additional information about the BI tool's environment, including the identity of the end user.
The following diagram illustrates how a BI tool handles and sends Alice's username when connecting to the data store via Satori, making Satori aware of Alice's user identity and enabling Satori to audit and enforce policies based on her true identity.
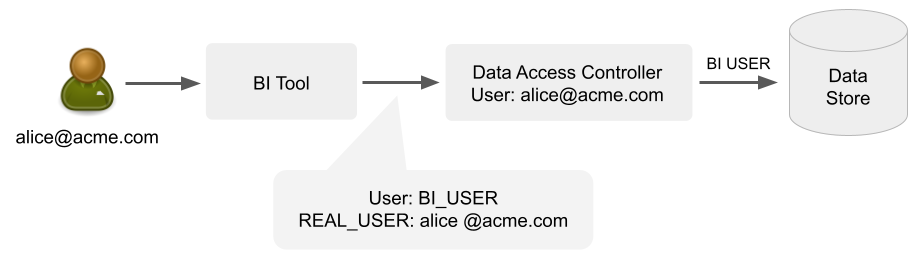
Looker Studio Support
Some datastores require require the Verify CA SSL mode (for example PostgreSQL, and MySql). To connect to these datastores from Satori, you may need to provision a root certificate to verify the certificates presented by the Satori DACs in your account.
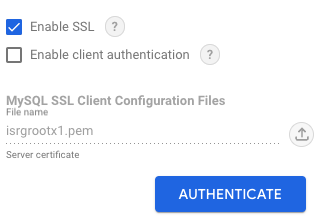
By default, Satori uses Let's encrypt certificates, the root CA certificate will need to be uploaded to Looker studio. The root certificate can be downloaded from here.
This screenshot illustrates what the file should look like. Upload this file to the Google Data Studio when creating a connection:
Looker supports sending additional parameters via JDBC connections. See the Additional Parameters section in the Looker documentation.
Note: Customizing the JDBC connection with additional parameters may disable Looker's PDT functionality. To ensure Looker's PDT functionality works correctly, make sure to override the Additional Parameters field with the previous value (without the
SATORI_LOGIN_NAME) in the PDT Overrides section, or specify a unique user ID to the Looker PDT. For example, in a Snowflake connection use:SATORI_LOGIN_NAME=LOOKER&SATORI_LOGIN_TOKEN=<TOKEN>.
Using Snowflake
To send the end user username to Satori, add the following parameter in the Additional Parameters field: SATORI_LOGIN_NAME={{ _user_attributes['email'] }}&SATORI_LOGIN_TOKEN=<TOKEN>.
To activate this functionality, you must first obtain an authentication token via the management console (Settings->User management->DAC Access Tokens) then replace the
Using PostgreSQL or Redshift
To send the end user username to Satori, add the following parameter in the Additional Parameters field: options="SATORI_LOGIN_NAME={{ _user_attributes['email'] }}""SATORI_LOGIN_TOKEN=<TOKEN>".
To activate this functionality, you must first obtain an authentication token via the management console (Settings->User management->DAC Access Tokens) then replace the
Using SQL Server
To connect Looker to Satori using the Satori service account credentials update the following parameters in Looker:
Username - select the Email option.
Password - copy the UUID Token value from the DAC Access Token tab in the Satori settings, for example: befdcb5b-e1b3-49e8-84d8-093116c9daf5.
PowerBI
Using SQL Server
To connect Satori with the PowerBI tool, create a new SQL Server connection and set the Satori URL as the server parameter.
For Example
server: abc123.us-east-1.a.s0.satoricyber.net and then press OK and enter your credentials.
Note: Unsecured connections are not supported (non-SSL driver option), to enable secure conectivity verify that the following settings are applied, perform thev following: - File -> Options and Settings -> Data Source Settings -> abc123-cluster-cajcpwqzmvbb.us-east-1.a.p0.satoricyber.net -> Edit Permissions -> Encrypt Connections
Using PostgreSQL
To connect Satori with the PowerBI tool, create a new PostgreSQL connection and set the Satori URL as the server parameter,
For Example
server: abc123.us-east-1.a.s0.satoricyber.net and press OK and enter your credentials.
Note: Unsecured connections are not supported (non-SSL driver option), to enable secure conectivity verify the following settings are applied: - File -> Options and Settings -> Data Source Settings -> abc123-cluster-cajcpwqzmvbb.us-east-1.a.p0.satoricyber.net -> Edit Permissions -> Encrypt Connections
Using Snowflake
To connect Satori with the PowerBI tool, create a new Snowflake connection and set the Satori URL as the server parameter.
For Example
server: abc123.us-east-1.a.s0.satoricyber.net and press OK and enter your credentials.
Note: Unsecured connections are not supported (non-SSL driver option), to enable secure conectivity verify the following settings are applied: - File -> Options and Settings -> Data Source Settings -> abc123-cluster-cajcpwqzmvbb.us-east-1.a.p0.satoricyber.net -> Edit Permissions -> Encrypt Connections
Tableau
Initial SQL
Tableau features an option to define an SQL command that runs whenever a new database connection is established. Satori utilizes a special SQL command to associate the Tableau users' identity with the connection.
To activate this functionality, you must first obtain an authentication token via the management console (Settings->User management->DAC Access Tokens) then add the below snippet with the newly created token as an initial SQL.
SELECT 1 -- 'satori_user: '[TableauServerUser]', satori_token: <TOKEN>'
Preset IO
Using PostgreSQL/RedShift
- Configure the DAC Access Token via the management console (Settings->User management->DAC Access Tokens)
- Configure the connection to the PostgreSQL/RedShift using SQLALCHEMY URI with the configured DAC Access Token for examp[le,
- Redshift
redshift+psycopg2://<USER_NAME>:<PASSWORD>@<SATORI HOSTNAME>:5439/<DATABASE_NAME>?options="SATORI_LOGIN_TOKEN=<TOKEN>" - Postgres
postgres+psycopg2://<USER_NAME>:<PASSWORD>@<SATORI HOSTNAME>:5432/<DATABASE_NAME>?options="SATORI_LOGIN_TOKEN=<TOKEN>" - Enable the user identification in the Preset IO, this will add a username comment to each sql query for user identification
Redash, Sigma, and Sisense (Periscope Data)
The integration to Satori is seamless, (i.e. no Initial SQL query is required), regarless of the datastore accessed, Redash, Sigma or Sisense will add a comment to the query that includes the users' metadata and will be associated with the connection.